What Does 'Trust Minimization' Mean in Ethereum Classic?
You can listen to or watch this video here:

The Vision of the Cypherpunks
When public key cryptography was invented at the end of the 1970’s the internet already existed and personal computers were about to hit the market.
By the late 1980’s and early 1990’s a group of cryptographers and computer scientists had already realized that, in time, although the internet and personal computing would revolutionize the world, that a centralized tecno tyranny would threaten basic liberties unless good cryptographic tools were invented to assure values such as privacy and sound money.
With this in mind, they formed an online mailing list, started calling themselves “Cypherpunks”, and began delineating what were the potential threats and planning designs to counter them.
What Are Trusted Third Parties
As cryptography assumes that the main threat are “evesdroppers” who may intercept messages and decrypt them, for Cypherpunks the threats were trusted third parties that intermediated in all of our affairs.
In the context of online interactions, trusted third parties would see all of our communications and activities, record them, and start profiling us politically or otherwise, and arbitrarily censoring our speech, deplatforming us, cancelling us, and controlling our behavior. Sounds familiar?
Trusted third parties may be banks who process our payments and hold our financial wealth, communications apps, social media apps, search engines, cloud services, and governments who may impose their agendas through these technology companies and services.
What Is Trust Minimization
So, the internet and personal computing presented two opposing phenomena: The opportunity of free speech and commerce on a global scale, and the threat of trusted third parties capturing us through the centralized technological platforms.
The solution that Cypherpunks envisioned was to minimize the trust needed third parties as much as possible using cryptography to avoid the control by corporations, governments, and special interests.
This goal was called “trust minimization” since, even with decentralized technologies, some trust is always deposited in third parties to relay the information.
The Bitcoin White Paper Mentions Trust Minimization 14 Times
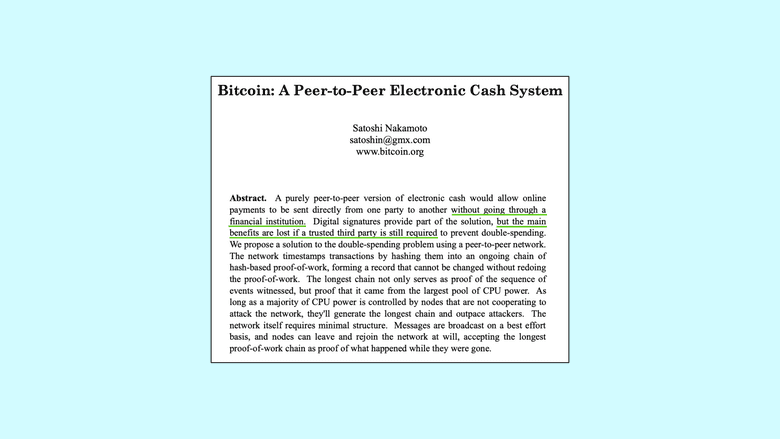
Within the efforts of seeking sound money on the internet, the first and most successful design to achieve trust minimization on a global scale was Bitcoin.
Trust minimization was such a central goal, that it was mentioned 14 times in the Bitcoin white paper.
In the case of money, savings, and payments trust minimization means to reduce the reliance in banks, central banks, and governments with regard to the issuance of money, processing of payments, and custody of the currency.
However, Bitcoin never evolved further than just being a ledger with accounts and balances. This implied that trusted third parties would still be needed to run external apps to use it.
Trust Minimization In Ethereum Classic
This is why it was such an important goal to recreate the idea of smart contracts that Nick Szabo had envisioned in the early 1990’s.
If in the real world everybody needed trusted third parties such as banks, escrow agents, payment apps, exchanges, property registries, and central banks, then it was necessary to attempt to replace these entities with online decentralized agents that would perform these tasks.
This is why Vitalik Buterin worked on, and came up with the idea of Ethereum Classic (the original Ethereum) in 2013, a smart contracts proof of work blockchain that would not only host accounts and balances as Bitcoin, but also smart contracts to power decentralized applications that would replace trusted third parties.
Examples of Dapps That Accomplish Trust Minimization
Smart contract powered decentralized applications (dapps) are the second most important invention in the blockchain industry because they finally accomplished the goal of minimizing trust in third parties.
Examples of dapps in ETC are:
Decentralized exchanges: Decentralized exchanges replace the need for brokers and traditional exchanges by providing on-chain liquidity pools that represent autonomous market makers that can trade with users enabling all sorts of token exchanges.
Non-fungible tokens (NFTs): NFTs are smart contracts that can represent online and offline assets, functioning as full service property registries, that are censorship resistant and permissionless.
Ethereum Name Services (ENS): ENS services on ETC replace the traditional DNS services and enable domain names on the blockchain that may be assigned to addresses or smart contracts to avoid the long and complex format of accounts on the blockchain.
A Warning of False Dapps
However, because smart contracts make blockchains such as ETC generalized computing platforms, this means that any kind of design may be hosted. And, this may even include centralized applications!
Examples of centralized applications may be:
Governance and voting tokens: Any applications that have governance or voting tokens are basically regular centralized entities, controlled by third parties, the voters, but where the back end code is hosted on a blockchain.
Stablecoins: Stablecoins look like decentralized applications, but the truth is that the custody of the external convertible assets, usually fiat currencies, always fully depend on off-chain trusted third parties.
Staking pools: Staking pools in proof of stake blockchains are not only centralized because those networks are centralized, but also because they have filtering mechanisms that select who can propose and validate blocks in those chains, and have governance systems that give their developer teams ample centralized decision making power over their systems.
Thank you for reading this article!
To learn more about ETC please go to: https://ethereumclassic.org
